This document covers how to:
- Calculate the vulnerability surface area of your software systems
- Understand how runtime architecture of each application affects business risk, vulnerability and severity
If this workflow doesn't sound like you, check out our document on managing vulnerabilities as a developer.
View the vulnerability surface area of your systems
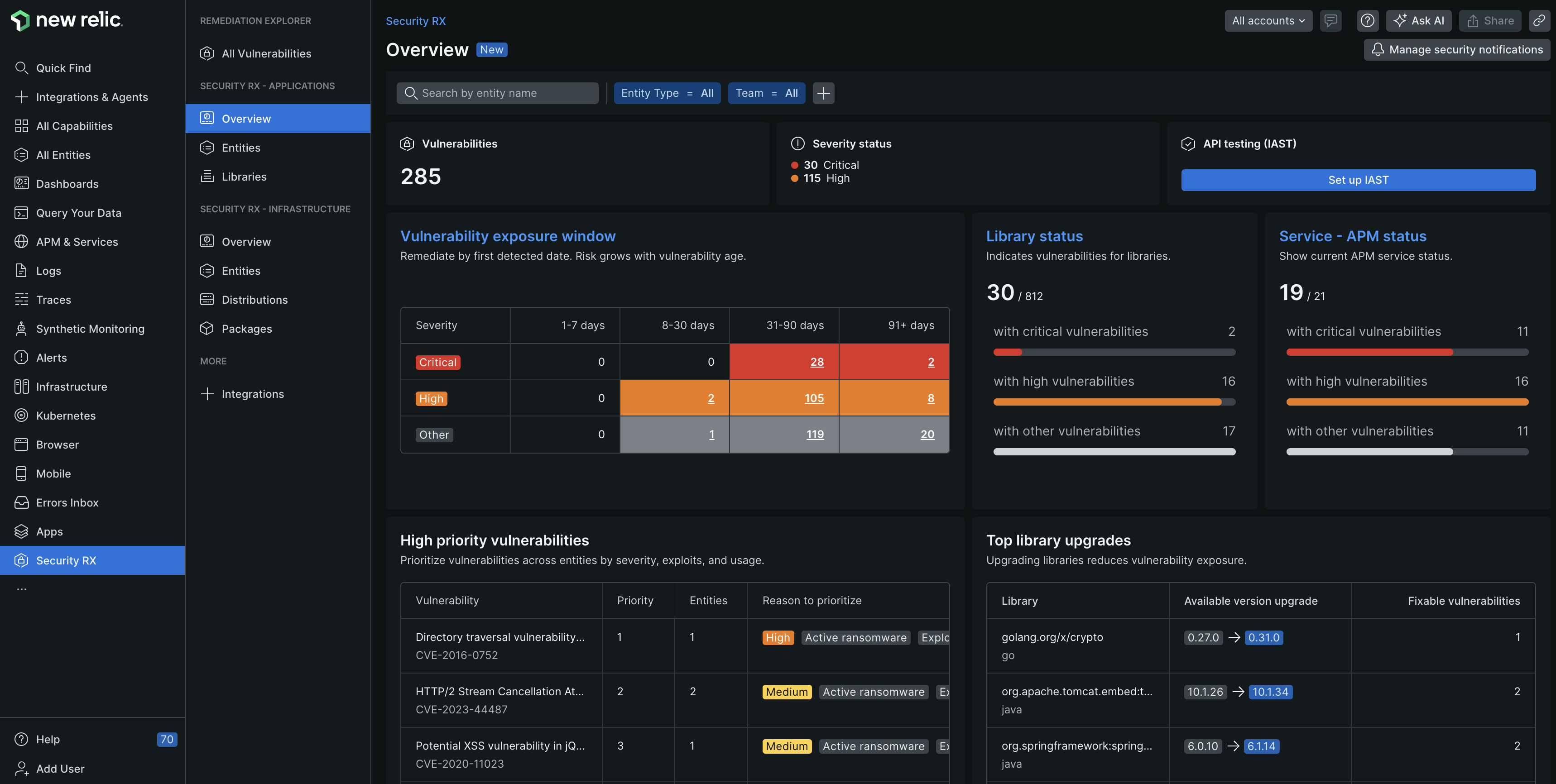
one.newrelic.com > All capabilities > Security RX
Once vulnerability data starts flowing into New Relic, you can access your data through various scoped views. To view a summary of your entire system, navigate to the Security RX capability > Security RX - Applications > Overview. This page provides curated dashboards representing the vulnerability of your system and baseline security hygiene.
Dig deeper into the security of your system by auditing the vulnerability of all your entities, libraries, and active vulnerabilities: